Encrypting a Document is intended to avoid access by unauthorized personnel. Attackers could easily access many relevant records, so it could be dangerous not to encrypt your PDF if it incorporates confidential data. Many PDF computer programs are capable of helping you add security requirements to your File types.
Here is just a majority of the best ten software tools commercially available for PDF encrypted communications. Wanting to protect your files and documents from infringement has now become more and more of a consideration. Hack current efforts and privacy infringements mean that exposure to your most sensitive information stored on computers is extremely easy than ever because of strangers.
Top 10 pdf encryption software that you can utilize
1. Axcrypt

Although software packages may be beneficial for many, it’s not quite as strong as paid products, so if you want anything trustworthy, AxCrypt is a great option. The platform was originally developed for entrepreneurs and corporate business professionals. It serves as protection, with documents being either secured by AES 64-bit or 192-bit cryptography, which should impede any intrusion. Google cloud features are also thrown in for good measure – the app can immediately secure files that are stored on sites like google chrome and Dropbox. There’s also passport communication, too, though, and then you can connect directly to your encrypted information through some kind of mobile application.
2. PDFelement
PDFelement is a competent PDF editing program able to scan, transcribe, arrange, and quickly integrate PDFs. It helps you to set the credentials to avoid illegal entry to PDF document editing. This operating system also has other awesome options that let you personalize directories, populate and characteristic features, and, therefore, more. Users can customize PDF documents from almost anywhere and safeguard them. Its simplicity puts adobe photoshop on a comparison with it, but it’s far more economical. It also allows you to carry out tasks in larger quantities. The brand has spoken for itself. Receive protection and partnership with PDFelement, as never before.
3. Folder Lock

While protecting the investments on personal devices is important, adding safety and security to any piece of hardware that retail locations, sensitive information is also extremely important. For example, most staff members on their mobile devices have direct connections to their email communications and other account information and really need protection. Folder Lock is an excellent option for introducing authentication to your android platforms. Your executable information, photos, videos, social connections, back pocket cards, documents as well as audio files collected in your smartphone can be protected by the android device. That there is not even authentication, but you can also establish a sniper username, ransomware countermeasures, record unauthorized login attempted, back up all your credentials, and be informed of possible malicious attacks.
4. Crypto expert
CryptoExpert is a desktop application platform that gives secure communications caverns for any and all your data, making sure that it is always safeguarded against possible breaches. It seems to provide more effective authentication than many of the other services and tools described in this worldwide web, flaunting equipment quality on-the-record. A wide variety of different databases can indeed be backed up by the system along with identity documents, Word, Excel, as well as word processor files, file types, and email database management systems.
5. Foxit PDF Security Suite
This specialized software synchronizes landscapes within Microsoft Rights business solutions. You could indeed savor dependable sensitive information points of support for doing more than merely fully accessible, edit and organize text. There is too much surveillance equipment inserted in this operating system that fits the needs of the company. It utilizes Foxit add-ins to protect Pdf documents and, while it may not be cost-effective with the specific use, it is a much more successful choice for businesses.
6. Adobe Acrobat
This app has been developed for individuals who really want to build and edit PDF files that contain confidential data. User accounts can be used to manage access to your files. Data protection of the records with that kind of PDF encryption tool is simple.
7. Certain Safe
CertainSafe is a relatively reliable cloud-based cryptography platform that aims to minimize all kinds of risks and complies with requirements from industries. You can preserve and exchange documentation, direct messages, photographs, images, and videos with the app, avoiding revealing them to external sources. The program also helps you to interact and connect with coworkers, with all communications authenticated. CertainSafe also keeps adding computer-controlled data protection for corporate systems and applications, which means you don’t just have to do small details individually. There is a special offer readily accessible for 30 days, during which membership costs $12 per a couple of weeks for 100 GB as well as up to 75 patrons available.
8. VeraCrypt
VeraCrypt is amongst the most serious security applications that give you business-grade encryption for critical documents. The framework is also quite easy when using, and just introduce usernames and passwords to your information collected and partition walls is all it seems to. Everything you must do is provide the program with some information about your information, such as quantity size, location, and designated cryptographic protocols-and then the software does its stuff. What’s nice concerning VeraCrypt too is that it would be invulnerable to brute-force bashing, so you have never had to think twice about cybercriminals authenticating your credentials and passwords information. The intuitive interface edition is fully free, too.
9. Secure IT 2000

Secure IT 2000 is a software for encryption techniques that penetrates your directories, too. The above implies it may take a little more time than some of the other applications, but it really does suggest that afterward, the documents may be more controlled. To reach any files, a central credential is needed, which may be somewhat restricted if you want to provide multiple keys for specific files, not particularly if you want to communicate any of them between colleagues and others.
10.Concealer
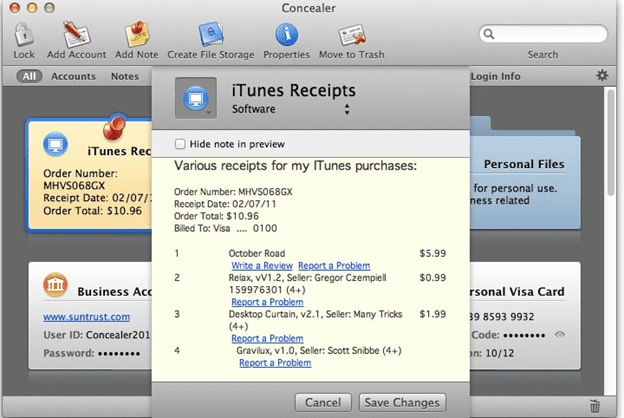
A concealer is a software that encrypts files pertinently for Apple desktop computers. Rather than just encrypting all files on your memory card, it presents you with an authenticated field to move files towards-which suggests you really have to make sure that you uninstall the autographed copy so as not to have both protected and weak encryption copies of your computer’s hard drive. You can also pick your desired strength of cryptography as 128 or advanced encryption standard. This credible cryptographic algorithms retailers card-shaped documentation and utilizes industry-standard personal information encryption standards (AES-256) to safeguard card details percentages, web page login details, proprietary software protocols, classified information files, and pictures and videos, and often more.
Conclusion
Later in the past, you may have used a cipher to encode something and then to burn the file if you promised to control a document hidden. And you could have it locked in a safe. Those options are complementary to the two major categories in encrypted communication public services.
Yet another type of item patterns files and directories and turns the others into unbreachable, cryptographic editions of their self. Then another creates an interactive graphics card that behaves just like every other computer on your device when it is opened. Once the virtual drive is closed, well, all files that you placed into it are totally unavailable. Whether copying a file into a permanent location or making a cryptographic hash of it, the unclassified initial must completely be wiped away.



